Bringg Access Management
Login and Authentication Methods
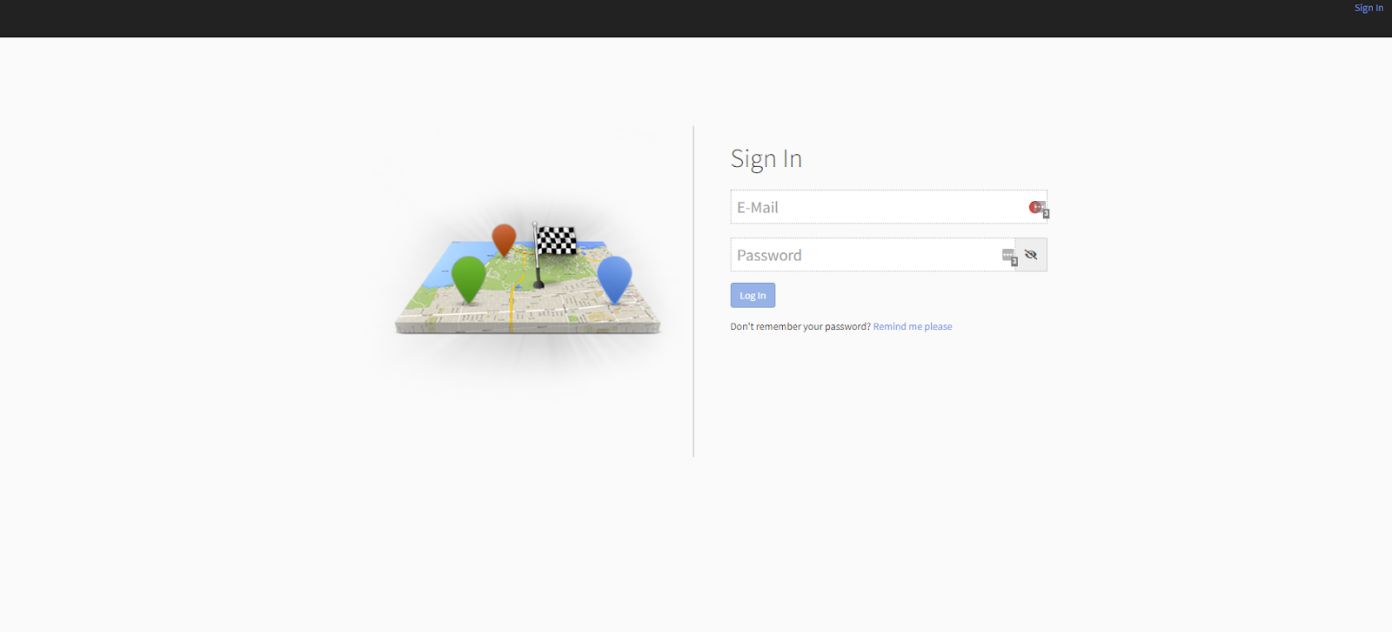
Bringg standard sign-in policy
-
An email address and password are required for standard sign-in to Bringg’s user interfaces.
-
Password requirements: minimum 4 characters (Store App min. 6 characters). No text/special character requirements.
-
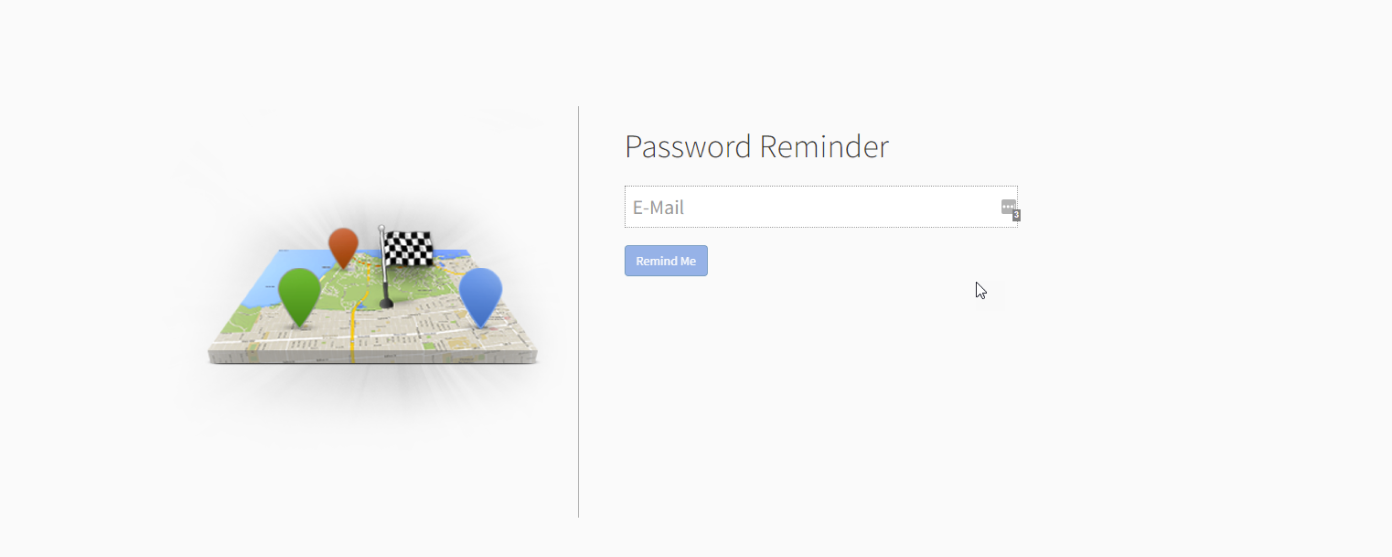
Reset forgotten passwords using the “Remind me please” link on the Sign-in page. You will receive an email from [email protected] (be sure to check your spam folder). Please note: The receiving email address must be registered to a Bringg merchant.
-
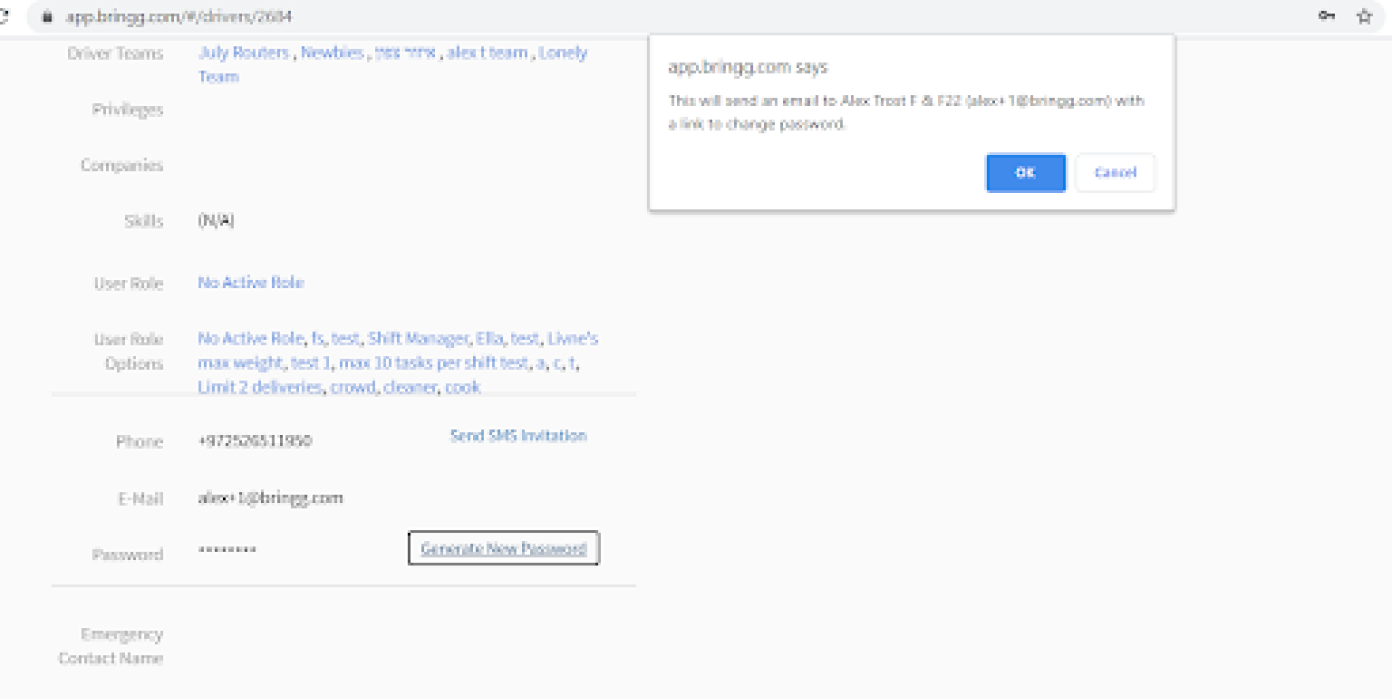
Both Admins and Dispatchers can reset another user’s password on the relevant User Page.
Key Considerations:
We strongly recommend using a valid email address for each user, rather than one with a fake or non-existent domain (i.e. [email protected]). These 'made-up' domains are frequently available for purchase and once registered can be used by malicious users to request password resets. This locks out legitimate users and allows malicious ones to gain access to sensitive customer and employee data.
Many of our customers create location-specific credentials on shared devices when it doesn’t make sense for each individual to log in to the system. For example: several different Dispatchers may use a single device to access Bringg Web simultaneously throughout the day, or a crew of three Drivers may be using a single-mounted device inside a vehicle. Please note: Location-specific credentials may be easier to guess than other types of passwords. To avoid any unauthorized access to your network or data, we strongly recommend using a random password generator and/or frequently changing your passwords.
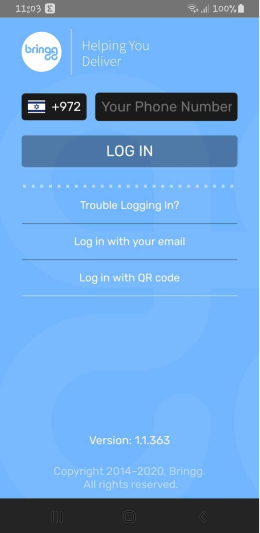
Sign-in using phone number & verification code
-
Enter phone number, if the phone number is registered to a merchant, the device will receive a verification code via SMS.
-
SMS verification codes are 4 characters long.
Debugging sign-in issues
- Make sure the user has a working internet connection (try to access a different web page on the device’s browser).
- Confirm the user’s details (e.g. email, phone number) are updated on the relevant user page.
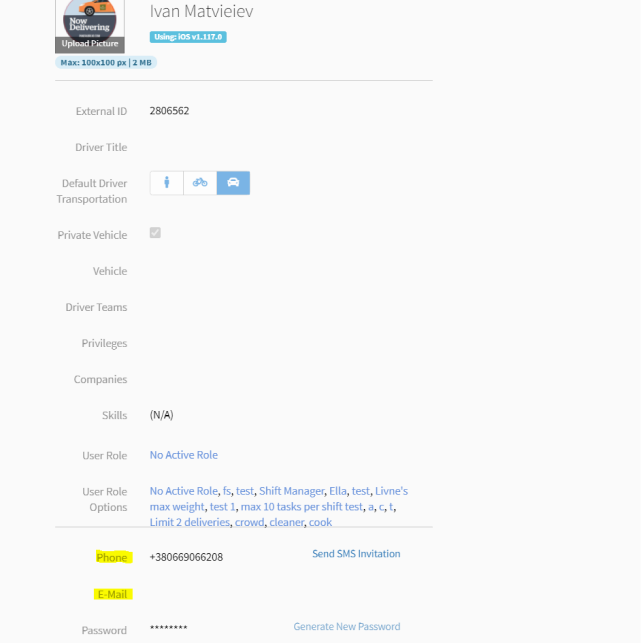
Sign-in using QR code
This feature allows Dispatchers and Admins to log in drivers by scanning a QR code. The QR code can be generated in Bringg Web through the Drivers Tab, the specific Driver’s user page or both, depending on the chosen configuration.
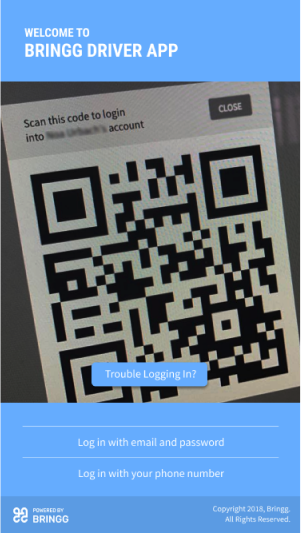
Keep in mind, QR codes should only be generated for Driver user types and may only be created in the Driver App. As an added precaution, it is not possible to generate a QR code for an assigned Admin user.
Multiple sign-in attempts via the same QR code are only allowed if:
-
The token is not expired - by default tokens expire 10 minutes after being generated.
-
The same device is trying to sign-in with the QR code - if another device tries to scan the same QR code, an unauthorized warning will appear.
It is also possible to generate QR codes independently, using the generate Driver QR_code API service.
Please note: Drivers who get logged out of the system while on the road will not be able to log back in using a QR code until they return to the home base.
Debugging issues with QR codes
-
Confirm that the user is assigned only a Driver user type.
-
Make sure the user has a working internet connection (try to access a page on the device’s browser).
-
Make sure no successful sign-in attempts were made using the specific QR (each QR code expires after a single successful login).
-
If the QR code doesn’t appear - test in Incognito Mode (Chrome: Ctrl + Shift + N); an ad blocker or similar extension/addon may be blocking it.
-
If the QR code doesn’t show in Incognito Mode, take a screenshot of the current page’s Console logs after clicking "LOG IN VIA QR" (Chrome: Ctrl + Shift + J).
Additional security measures
Lock users after multiple sign-in attempts
It’s possible to configure the Max Failed Login Attempts Limit. Once a user exceeds the Max Failed Login Attempts Limit any further attempts will be blocked and the user’s account can only be unlocked by an Admin
ReCaptcha
Bringg will challenge users to correctly complete a Captcha when:
- Four failed sign-ins are attempted within a predefined time range
- The first Captcha attempt selects the “I am not a bot” box
- Google detects unnatural mouse movement
Please note: The Internet network must allow access to *.google.com for successful submission of Captchas.
Secured setup
Secure setup allows for the following access security enhancements:
Use registration API to generate a password for users using the following options:
- A notification email with a create password prompt.
- The user is initially created with an assigned temporary password. Upon first sign-in the user is prompted to create a personal password.
Admins and Dispatchers are automatically logged out of Bringg Web after a period of inactivity.
Changing a user’s user type (e.g Dispatcher to Admin, or Admin to Dispatcher) requires a reset of the user’s password.
The SMS verification code includes 6 characters.
For full details on the secured setup feature, please consult your Bringg representative.
Single sign-on / single log-off (SSO/SLO)
Single sign-on is an authentication scheme that allows a user to log in with a single ID and password to any of several related, yet independent, software systems. Bringg implements SSO and SLO using your organization's Identity Provider (IDP) along with the list of fields defined as the identity authorization keys.
Bringg complies with SAML for Bringg Web apps and OpenID for the Driver App.
For SSO/SLO to be effective, it is necessary to disable the option for authentication through other methods. However, specific users and/or teams can be excluded from the SSO/SLO. This allows users who are not in your IDP to connect to Bringg (e.g. contract employees who need access to Bringg but do not need access to any other organization systems).
Debugging issues with SSO
Debugging issues with SSO varies depending on the chosen software and integration method.
-
Confirm the user’s details match in both the IDP and Bringg user page.
-
Confirm that Bringg has credentials or a mechanism to replicate SSO authentication.
Updated 9 months ago
